Many devices for the Internet of Things (IoT) will need to transfer data securely, demanding the use of cryptographic algorithms and secure key storage. Some of those keys will be used to gain access to important services that, potentially, can be used by cybercriminals to launch attacks on a network or gain a financial advantage. For example, a meter that reports usage of a resource such as energy can be tampered with to reduce the bill.
As a result, it is extremely important that any secure keys are protected effectively so that they cannot be retrieved and misused. Unfortunately, there are techniques that make it possible for unprotected systems to be compromised.
Electronic circuits produce a variety of emissions as byproducts of their processing that make it possible for an attacker without detailed knowledge of the actual structure of the circuitry itself to deduce what data it is processing. Heat and electromagnetic emissions are both viable sources of information for an attacker. As these emissions are side effects of operation, the use of them to perform reverse engineering has earned the term ‘side-channel analysis’.
All attacks take advantage of the changes in processing behavior that will be exhibited at different times during algorithm execution. There are two broad classes of side-channel analysis: simple and differential. Within those classes, attackers can use a range of side-channel properties, such as the heat generated, power consumed, or execution time. For example, naïve algorithms may return early from comparisons, indicating to the attacker which bytes within a password are wrong.
Software implementations of cryptographic algorithms may also demonstrate timing variations that depend on the state of bits within a key because operations can vary in complexity depending on the key value. Another issue with software code is that on-chip caches can affect timing in ways that allow an attacker to obtain information about the data being processed.
Developers have implemented a number of countermeasures designed to fend off side-channel attacks – by equalizing execution times and logic activity – as well as by performing further encryption steps that alter the Hamming distance between successive data words sent across the on-chip bus. As the capacitive loading experienced by the bus depends heavily on Hamming distance, and this change in loading is exhibited as comparatively large EMI and heat spikes, this type of activity is a key target for side-channel attacks. Whereas altering the balance of logic can negate timing-based attacks, defenses based on disguising the Hamming distance can deal more effectively with EMI and heat-based attacks.
As countermeasures improve, attackers are moving to more active techniques in which they attempt to disrupt the normal behavior of the target in the hope of revealing data. Key attack vectors are the clock signals and power rails. Stopping the clock in mid-cycle and then restarting it is one key technique. Another is temporarily reducing the supply voltage to below the point at which transistors are able to switch properly. These techniques can lead to aberrant behavior and data corruption.
For example, a microcontroller’s central processing unit (CPU) can execute instructions incorrectly and lead to unexpected activity on the internal data-address and control lines. This can, in turn, cause CPU registers, I/O registers or memory to become corrupted. This corruption is helpful to an attacker as small changes in the data fed to the system coupled with carefully timed power glitches can be detected as changes in processor or circuit behavior compared to normal operation.
It is possible to design circuits that defeat clock-based attacks on encryption hardware by using an internal clock source. Only well-funded attackers with the ability to physically probe the chip can alter the clock at will. However, there is no simple way to prevent an attacker with access to the hardware from interfering with the power rails, as there are few, if any, practical ways to integrate an energy source with the IC.
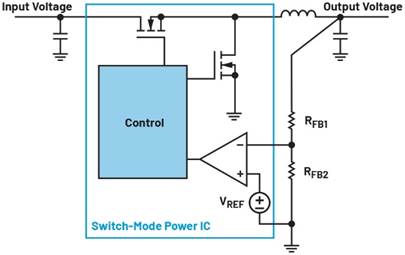
To avoid problems caused by sudden losses of power, the processor or encryption circuitry should be prevented from operating for the periods of insufficient voltage, often called ‘brownouts’. An effective way of ensuring this is to use an external power-supply low-voltage or brownout detector. Below a programmed threshold voltage – which may be 5 to 15 percent below nominal – that lasts long enough to cause problems, the detector toggles the reset pin, which will stop execution. This forces the processor and related circuitry into a known state and prevents internal program, control and data accesses.

Figure 1: A simple low-power external brownout circuit suitable for resetting MCUs such as Atmel’s AVR series.
When the supplied voltage rises past the threshold for a sufficient length of time, the reset pin is released and the protected circuitry starts from a known reset state. Typically, this will remove any volatile data and restart execution from the system’s start point. Any tasks that were in progress up to the brownout will need to be re-started, as registers will typically be forced to their default states. Reset may also have the effect of wiping internal SRAM, which is the safest option, as the brownout may cause individual cells to lose their contents as this type of memory relies on a constant power source.
The restart caused by a reset being toggled has the effect of forcing the attacker to start from scratch after any attempts to disrupt power and reduce to the bare minimum what they can determine about the internal state of the device when each brownout is triggered.

Figure 2: A typical response curve for the reset signal using a simple low-power detector.
There are a number of approaches to detecting brownouts that can provide the necessary reset control that can be built discretely. However, there are potential downsides to the discrete approach. Building a circuit with the necessary combination of responsiveness and reliability can be difficult. A key problem is what happens if the power supply oscillates around the trigger point, which may lead to the device moving in and out of reset in rapid succession and cause other problems.
Alternatively there are off-the-shelf devices that include support for hysteresis to prevent the problem of oscillation around the trigger point. A number of microcontrollers, such as the AVR series from Atmel, also include brownout detectors.
The ICL7665 from Maxim Integrated warns microprocessors of both overvoltage and undervoltage conditions and supports programmable hysteresis conditions as well as voltage thresholds to ensure that the voltage has stabilized sufficiently to allow the processor out of reset. The trip points and hysteresis of the two voltage detectors are individually programmed using external resistors to any voltage greater than 1.3 V. The ICL7665 will operate from any supply voltage in the 1.6 V to 16 V range, monitoring voltages from 1.3 V to several hundred volts. The Maxim ICL7665A offers improved accuracy with a threshold accurate to within 2 percent and guaranteed performance over temperature. The 3 μA quiescent current of the ICL7665 makes it suitable for voltage monitoring in battery-powered systems, typical of IoT applications.

Figure 3: Use of the Maxim ICL7665 for threshold detection.
Providing a watchdog timer function in addition to power monitoring – to allow for the monitoring of system software for possible problems caused by glitching other than power-rail disruptions – the MCP1316 made by Microchip Technology will hold a device in reset until the voltage has stabilized. The device supports hysteresis to avoid reset being exited too soon if noise on the supply rail is causing the voltage to move quickly above and below the trip point. Internal delay circuitry will hold the reset until the appropriate reset-delay time has elapsed.
Also providing the combination of watchdog timer and power-rail monitoring, Texas Instruments’ LM3710 has separate power-fail and brownout detection outputs. The former can provide advance warning of a brownout when routed to a voltage divider that monitors an external power input. Whereas the power-fail warning may be used to bring the protected circuitry into a hold state, the brownout input will typically be used to drive a reset signal.
As well as ensuring that the power rails are not vulnerable, it is worth noting that package choice can also have an effect on the immunity of IoT hardware to attacks. Most silicon devices are susceptible to photons, particularly infrared, and so can be disrupted by strong lights being shone on the die. Traditional plastic packages provide effective protection against this problem but it is not the case where the die can be exposed to light, which can happen with some chip-scale packages such as DSBGAs.
By paying attention to the susceptibility of the power rail to attacks, IoT device developers concerned about the integrity of their systems can reduce the risk of encryption keys and other sensitive data being exposed, assuming they have taken other precautions to counter side-channel analysis and other forms of reverse engineering.