Data security is rapidly becoming an overarching concern in a wide range of low power and portable applications, especially those reliant on wireless connectivity. Wearable devices for medical and health monitoring applications collect and transmit personal data. Industrial wireless sensor networks used in manufacturing, smart buildings, commerce and transport networks operate by transmitting sensitive data that may be vulnerable to theft, tampering, espionage or vandalism.
Often powered by energy harvesting, such applications require ultra-low-power operation, smart power management and small size. Implementing sophisticated security features into such highly constrained designs presents a potentially tough challenge.
This article will consider some of the security options open to developers of energy-harvesting-based wireless sensor networks and ultra-low-power portable products. The first is microcontroller-based solutions incorporating data encryption and other security features. Another involves dedicated authentication devices and software. Further aspects include judicious choice of wireless protocol and network architecture, both of which can play an important role.
Featured products include microcontrollers based on the ARM Core-3 MCU, such as the STMicroelectronics ST32 series and Maxim’s MAX32600 Wellness platform. Dedicated devices include Maxim’s MAX66242 Deep Cover Secure Authenticator. Linear Technology’s Dust Networks SmartMesh ICs and modules, meanwhile, use a mesh network topology to provide security in IPv6 and WirelessHART wireless sensor networks in industrial applications.
Sensitive data
The ‘Internet of Things’ movement may well improve our lives in many respects, be it in health and fitness monitoring, traffic management, smart buildings or industrial control. However, with an increasing amount of personal and sensitive data transmitted wirelessly to and from the cloud, robust data security is fast becoming a critical concern. Building systems that are secure, tamper-resistant and protected against attack is essential.
Data security in any system can be enhanced through the appropriate choice of microcontroller. ARM’s Cortex-M3 core is a good example. Not only is it very low power, yet powerful, it also supports features such as public key authentication, data encryption and tamper detection. The core has been implemented by many microcontroller vendors including Analog Devices, Atmel, Cypress, Energy Micro, Spansion, STMicroelectronics and Texas Instruments, and has been incorporated into application-specific solutions, SoCs and FPGA-based systems.
ARM has been a leader in data security for embedded systems for over a decade with its TrustZone and SecurCore technologies, which have been widely adopted, supported and enhanced by ARM partners. Properly implemented, these ARM cores can help protect code and data, through hardware and software, in any part of an embedded system.
STMicroelectronics offers several families of secure microcontrollers based on the Cortex M3 core as well as ARM’s SC300 SecurCore technology. ST is actively addressing the growing demand for data security in low power computer, industrial and consumer markets by providing secure MCUs with appropriate form-factors, interfaces, operating systems and management systems.
ST’s devices incorporate a TPM (Trusted Platform Module) compliant with the TCG (Trusted Computing Group) industry standard, and embed a highly secure proprietary operating system (AuKey) to help protect user assets and guarantee platform integrity. AuKey is aimed at manufacturers who wish to protect their brand against counterfeit, cloning or any illegitimate use. The company claims that secure MCUs with a USB interface provide a highly integrated solution for token-based secure applications. Combined with ST’s NFC devices, ideal for energy harvesting products, they can also be used for secure contactless reader systems.
The STM32F range, based on the Cortex-M3, is designed specifically for low-power operation. The STM32F1 series is a 32-bit, 1.8 V microcontroller operating at 72 MHz, featuring 384 kB flash memory and supporting a range of interfaces, including USB.
Health monitoring
The ARM Cortex-M3 is at the heart of the new ‘Wellness Platform’ developed by Maxim Integrated (See Figure 1 below). Voted ‘Electronica 2014 Product of the Year’, the MAX 32600 incorporates a 24 MHz M3 with 256 k flash memory, 32 k SRAM and 2 k instruction cache, as well as highly integrated analog peripherals. (An evaluation kit MAX32600-kit is available).

Figure 1: Maxim’s MAX32600 Wellness Platform for health monitoring is based on the ARM Cortex-M3 secure core, and features a Trust Protection Unit for added data security. The platform supports ultra-low-power battery operated and energy harvesting applications.
Exploiting the core’s security features, the platform includes a Trust Protection Unit for ‘end to end’ security, providing an AES hardware engine and fast erase SRAM for secure key storage, among other security and protection functions.
The platform is specifically designed for wearable, battery operated and energy harvesting applications, with ultra-low system power (175 µA/MHz in active mode, <1 µA in low power mode). Applications include electrocardiogram response, blood pressure, temperature, blood oxygen content, heart rate and activity level, and a number of reference designs are also available.
The Temperature Patch, for example, uses a passive NFC tag powered by RF energy harvesting, to measure patient temperature on a continuous and non-invasive basis. The device features Maxim’s latest DeepCover Secure Authenticator IC, MAX 66242, specifically aimed at the secure collection of data from portable devices. With RFID/NFC and I2C interfaces, it is expected to prove especially useful in medical/wellness and asset tracking applications where there is no space to provide a connector for external functionality. The device can be used to extract data securely from a slave device even when it is powered off.
DeepCover is Maxim’s embedded systems security solution incorporated into some of its microcontrollers, including its M3 core-based devices and stand-alone secure authenticator chips for low-cost IP protection, clone prevention, and peripheral authentication. The DS28EL15 is one of a number of Maxim’s current range of DeepCover Secure Authenticator ICs for sophisticated security and protection of data memory. An evaluation kit, the DS28EL15-EVKIT is available for development purposes.
Wireless security
The choice of wireless protocol is another important aspect of ensuring data security in portable applications. Bluetooth is popular, but has been reported as more susceptible to hacking than other protocols. Some of the techniques noted above can improve security in Bluetooth applications considerably. However, in other sectors outside of consumer, alternative wireless protocols have been shown to be more reliable and easier to secure.
Both Internet Protocol (IPv6 or 6LoWPAN, using IEEE802.15.4) and WirelessHART are widely used in industrial applications, claimed to operate securely in harsh RF environments and, importantly, at very low power. For some years, Dust Networks’ SmartMesh IP embedded wireless mesh sensor networks have been used to provide secure networking in manufacturing, process control, transportation and mining applications.
Now part of Linear Technology, the SmartMesh IP system is based on the LTC5800 SoC, (coincidentally integrating the ARM Cortex-M3), for IEEE802.15.4 wireless mesh networking. Several layers of security are provided via smart algorithms to deliver encryption for data confidentiality, high data reliability for integrity of message and authenticity. A range of sensor ‘motes’ and modules are available, designed to operate from very low power, giving battery life of 10 years or more. Network manager components are provided for building robust and secure wireless sensor networks. Supporting either 6LoWPAN or WirelessHART protocols, the devices and modules are easily integrated and evaluation boards are available.
The LTC5800IWR-IPMA is an example of a SmartMesh IP protocol mote, while the LTC5800IWR-PRB is the manager. The LTC5800IWR-WHMA is the WirelessHART mote. Starter kits, demonstration boards and development boards include the DC9007A, WirelessHART starter kit, complete with seven boards and cables and the DC9003A-C WirelessHART demonstration board.
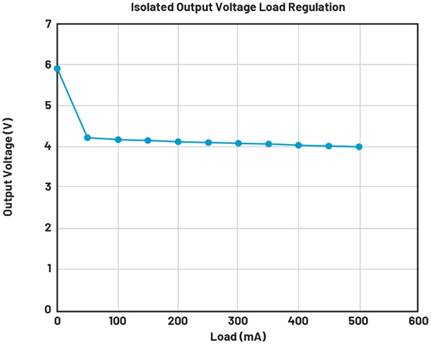
Linear Technology provides a useful ‘How to’REF1 article covering the operation of a temperature sensor, powered by energy harvesting, as part of a secure IP-based mesh network. It uses the LTP5901 SmartMesh IP module containing radio, networking firmware, microprocessor and power sequencing manager. The application also uses the LTC3330 low-power dual switch mode power supply that derives the power from the energy-harvesting source (i.e. solar panel), reverting to battery power when needed to maintain output regulation. See Figure 2 below.

Figure 2: Block diagram of wireless temperature sensor, powered by harvested energy, connected to a SmartMesh network via the LT5901 and controlled by the LTC3330 power supply with LDO.
Conclusion
Energy harvesting is rapidly gaining in popularity for wearable and wireless sensor network applications. Protecting sensitive data that is transmitted across wireless links is becoming a critical design factor in a growing range of industry sectors as the ‘Internet of Things’ movement takes off. Personal data collected by health and fitness monitoring, wearable and implantable medical devices must remain confidential. Increasingly automated facilities are taking advantage of ultra-low-power wireless sensor networks to increase efficiency and save energy in factories, smart buildings and in environmental monitoring. Protecting data against theft or potentially dangerous tampering is paramount.
This article has highlighted a number of easy to implement solutions based on considered design choices involving secure MCUs as well as wireless protocol and network topology.
References:
- Linear Technology How to Article: Precise Wireless Temperature Sensor Powers Itself.